Imagine being a CISO, hauled into a boardroom, and asked: “Why is your team using a collaboration tool that isn’t even end-to-end encrypted?”
Where would you go with that?
- “The team is familiar with Slack; I didn’t want the pushback from replacing it.”
- “Microsoft Teams is bundled for free.”
- “It was here when I arrived, and it never made the To-Do list.”
- “The taps always drip in the plumber’s house, and the cobbler’s kids are notorious for running around barefoot.”
While there’s a fair amount of truth that you “never get fired for buying [insert big brand],” there is far more truth in “you definitely get fired for failing to take basic precautions that make getting breached far harder.” Although to be fair that doesn’t trip off the tongue.
The de facto standard is substandard
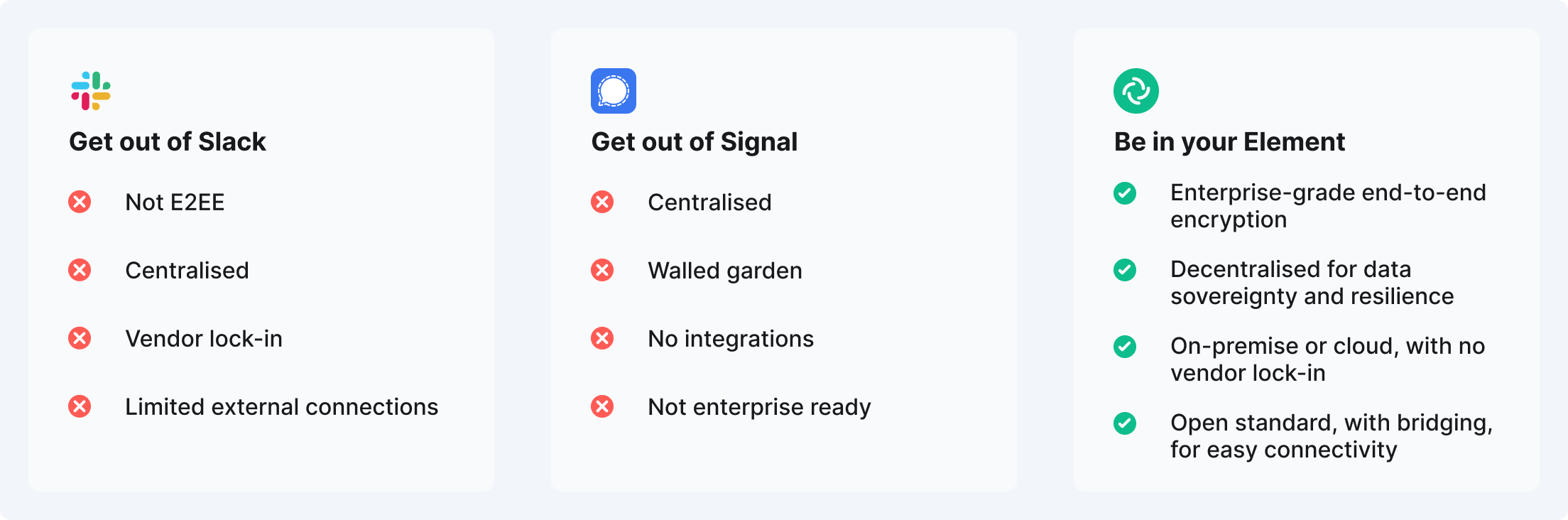
It makes no sense, but most cybersecurity teams use a combination of Slack and Signal.
Slack isn’t even end-to-end encrypted - leaving everything on display to anyone who gets inside. And while Signal has E2EE, there’s zero enterprise functionality (given that Signal has never intended to be an enterprise app). On top of that, both are centralised systems - creating single points of vulnerability and making themselves a huge attack target.
The battle to replace de facto standards
The difficulty, especially in large organisations, is convincing others of the need to upgrade to something that is actually fit for purpose.
So we’ve created a guide that hopefully gives you all the content you need to reassure various layers of bureaucracy, and help navigate through your internal processes to get the right choice in place.
It asks a few simple questions to get colleagues on board, including:
🗣 Does your collaboration platform provide a fundamental layer of security so you know who you’re communicating with?
Unless it’s end-to-end encrypted and offers cross-signed device verification, it’s a no. Both are needed to create a truly secure messaging platform. Working side by side, they ensure that your conversations are protected and in turn give you the confidence that you’re talking to the right person.
🔒 Do you have complete ownership of your data?
If you’re using a traditional centralised SaaS platform, then the likelihood is no. An on-premise solution, or a data sovereign preserving hosting service, are the only ways to ensure genuine data ownership. Not only does that make you more secure but, if built on an open standard, it also gives you the independence to choose between on-premise or a variety of hosting services.
🤝 Can you communicate easily with your external network of cybersecurity experts?
If you’re looking at walled gardens such as Slack and Signal, the answer is no. Think about how you can email anyone, regardless of what email client people might be using. That’s what the Matrix open standard delivers - the interoperability you associated with email, but with the security of end-to-end encryption.
💪 Is your platform resilient in the face of adversity?
Centralised systems are prone to global outages, so for Slack, MS Teams or Signal it’s a no. The decentralised design of Element and Matrix that delivers data sovereignty also creates a far more resilient network.
We know, like you, that real time communication is crucial for cybersecurity, and the sensitivity of the discussion demands end-to-end encryption and complete data ownership. Slack and Microsoft Teams deliver neither.
Cybersecurity teams should be among the first to take advantage of a new era of enterprise-grade encrypted collaboration and messaging.
Element gives cybersecurity teams end-to-end encryption by default and an open network for easy, secure connectivity inside and outside the organisation. And the cybersecurity team retains complete ownership of its data and conversation, whether deploying on-premise or being fully hosted and managed by Element.
So download the guide and see if it helps oil the cogs of the corporate decision-making machine.


