Advancing Secure & Convenient Government Communications: The Case for Element
The recent incident involving the inadvertent inclusion of a journalist into a Signal group chat where US officials discussed sensitive military operations highlights the complexities governments face when using consumer messaging applications for official communications.
Historically, various government administrations have used commercial messaging apps for official purposes. For example, Boris Johnson’s administration, and Macron’s team before France chose to standardise on Element.
Sweden recently encouraged its Armed Forces to use Signal, the EU recommended Signal too, and just last week The Office of the Australian Information Commissioner released a report showing extensive use of Signal and WhatsApp within its government.
The attractiveness of consumer messaging apps to government officials is often driven by their convenience and familiarity. The apps are widely used in their personal lives, and officials naturally seek out a seamless way to communicate with colleagues. The increasing expectation of instant communication can also drive officials to use the apps, as people now anticipate rapid responses and updates around the clock.
But Signal, WhatsApp, and other common commercial messaging apps offer absolutely no control over who is in a chat group, nor do they consistently ensure that their identity is who they really claim to be. There’s also no record keeping, which means a lack of compliance and information governance nightmares. In this instance, the conversation could violate either the Presidential Records Act or Federal Records Act.
The reality of these dangers is quickly coming into focus. It was recently urged by Senators Ron Wyden and Eric Schmitt to move away from insecure centralised platforms and instead adopt the decentralised Matrix protocol for sovereign, secure and interoperable communications.
Why this would never happen with Element
A proper government deployment of Element takes advantage of Element Server Suite (ESS), an enterprise-grade backend that gives the IT function all it needs to professionally manage its platform and end-users. Within ESS are Advanced Identity and Access Management features that enable an Admin to restrict the sets of people who are allowed to participate in a given conversation, linking it through to an existing directory system such as LDAP or Microsoft Active Directory.
Crucially it ensures that as users are onboarded and offboarded they are only given access to relevant conversations, as specified by the end-user organisation. So, no accidental invites to random people, such as journalists or foreign spies. You'd also require verified identity to ensure that only users whose online identities have been explicitly verified to belong to the expected person would be able to participate in the conversation (or indeed voice/video calls and conferences). If required, you could also archive the conversation to comply with public record keeping legislation through Auditing functionality, or apply Data Loss Prevention (DLP) rulesets to ensure sensitive data isn’t accidentally leaking at the wrong classification.
Moreover Element Server Suite would be run on a dedicated instance hosted specifically for the personnel in question, potentially configured to (privately) federate with other governmental deployments at the same classification through the use of Secure Border Gateways, or Cross-Domain Solutions for high-side and low-side environments. There’s even air-gapped options specifically for high-side environments. Built for huge government deployments, optimisations within ESS enable it to cost efficiently support literally millions of end-users if needed, with multiple back-ups and fail-overs to ensure continuous uptime.
That said, it’s worth noting that the fact that Element lets you run your own communication service can be a double-edged sword. It’s obviously a positive that Element Server Suite provides a commercially supported, best-in-class enterprise distribution which lets organisations operate deployments with full peace of mind. However sometimes we see critical deployments improvise their own setups by freeriding on Element’s community open source components. This introduces significant risks, with the deployment then deprived of access to Element’s support, best practices, advanced security advisories, audits and accreditations - and without any of the high-availability, scalability and enterprise functionality (e.g. group access control) found in Element Server Suite. In-house teams and irresponsible systems integrators beware…
Why do governments use consumer messaging apps?
Senior politicians are not technologists. Like most other people they just default to the quickest and easiest solution, and feel safe because messaging apps wave end-to-end encryption around as though it’s a silver bullet. The fact is people like consumer-style, easy to use apps. No one has ever downloaded Microsoft Teams, Webex or Salesforce to their phone because they like it. Given a free choice they choose something like WhatsApp or Signal.
People’s preference for the usability of consumer messaging apps is natural, but within government - or any workplace - it creates shadow IT. You can only address it with beautifully usable, consumer-style apps that hide all the enterprise-grade complexities a government solution needs behind a simple and familiar user interface. It’s precisely why we invest so heavily in user experience (hence Element X). People simply don’t put up with clunky tools in the name of security.
Why are consumer messaging apps unsuited to government use?
Governments need to ensure their digital sovereignty, which should eliminate the use of vendor-controlled cloud-based solutions in favour of self-hosted solutions. Genuine digital sovereignty also requires open source software, for complete auditability and to protect against vendor lock-in. The need for interoperability - which is absolutely critical for communications - makes siloed solutions unsuitable.
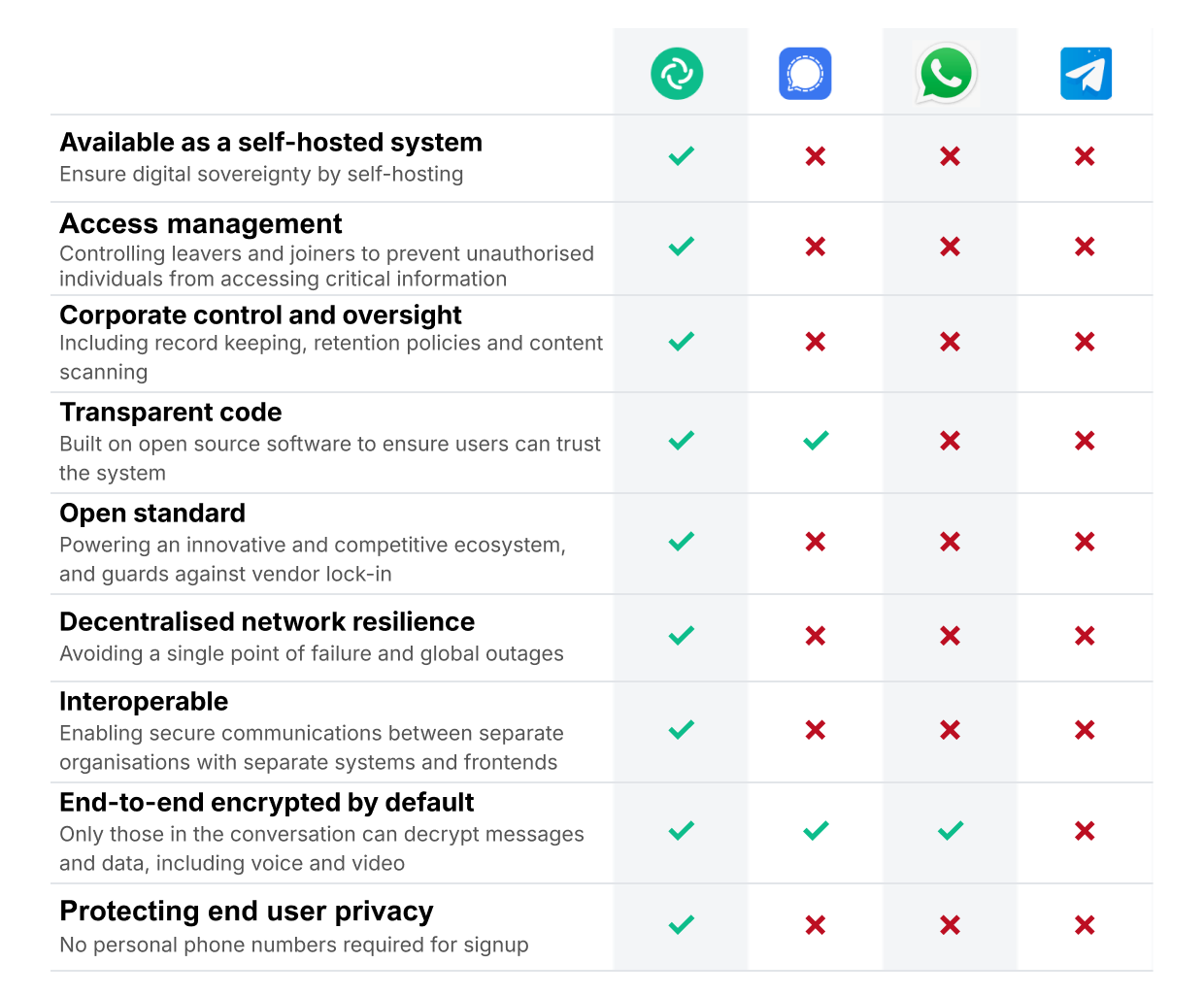
| The problems with Signal |
|
| The problems with WhatsApp | WhatsApp presents governments with all the same problems as Signal, as well as:
|
| The problems with Telegram | Telegram presents governments with all the same problems as Signal, as well as:
|
None of the above is to discredit the technical security of Signal. It has a strong security posture, encompassing end-to-end encryption, minimal metadata, and other privacy-preserving features. But this story just shows that security - especially national security - goes beyond privacy features. Organisations need to be able to restrict who is allowed to participate in given conversations, and guard against fat-fingered invites. Governments need to be held accountable for the technology they use. Complex military operations require appropriate records, audit trails, and the ability to retrieve records. They most definitely cannot be managed in the Wild West of a consumer messaging app.
How else is Element different?
Element is uniquely placed to serve governments. It uses the Matrix open standard to provide the cornerstones of digital sovereignty, security and interoperability - and then builds on that to give public sector organisations the same oversight and control of their deployment that they would expect from other corporate solutions.
The decentralised Matrix protocol enables an end-user organisation to own, host and control its solution and data. It also ensures more robust and reliable communications than a centralised technology, especially in moments of crisis and break-down of intercontinental connectivity.
Taking digital sovereignty a step further, both Matrix and Element are open source, which gives end-user organisations the transparency to be able to trust their communications platform. And because Matrix is a popular open standard, end-user organisations also benefit from a competitive ecosystem helping to drive innovation and protect against vendor lock-in. Perhaps most important, the open standard interoperability Matrix delivers allows each party to use their own solution, while still being able to federate and communicate securely with each other. That’s very much how SMTP works for email, only for secure real-time communications that standard is Matrix.
A new era of secure government communication
Progress isn’t linear. Encryption goes back to at least Ancient Egypt. Modern day end-to-end encryption dates back to the arrival of Pretty Good Privacy (PGP) in 1991. The iPhone launched in 2007, Signal was released in 2014. The Covid pandemic, which really drove the use of consumer messaging apps within the workplace, struck just five years ago.
The French government began rolling out Tchap, its French-branded fork of Element, in 2019. Germany’s Armed Forces started to deploy BwMessenger, its German-branded fork of Element, at the very end of 2020. The US Department of Defence started using Element in 2020. NATO ACT began investigating Element in 2023 and created NI2CE Messenger, its branded fork of Element, in 2024. The United Nations International Computing Centre (UNICC) selected Element as its secure communications platform in 2024.
As more and more governments realise that their use of consumer messaging apps presents unacceptable risk, we’ll see the proliferation of Element and other Matrix-based communication across governments worldwide ushering in a new era of sovereign, secure and open standard based real time communication.
*This blogpost was updated on 31 March


