What it really means in MS Teams, Signal and Element
Not all E2EE is created equal
End-to-end encryption (E2EE) is a foundational feature for secure digital communication, ensuring that servers can never see your conversation data - even if breached or legally forced. Unfortunately, it’s a term that has been repeatedly distorted - Microsoft Teams claims to be end-to-end encrypted when in practice support is partial at best. As more enterprise tools add E2EE to their feature list, it's important to unpack what that claim actually entails — and what it doesn't.
At Element, we’ve seen many organisations assume that Microsoft Teams offers encryption equivalent to that of Signal or Element. This isn’t the case. This article offers a neutral, fact-based comparison to clarify the real differences in E2EE implementations between Microsoft Teams, Signal, and Element.
E2EE feature comparison
While Microsoft Teams does support end-to-end encryption in certain contexts, it is limited in scope and does not apply to the majority of everyday usage. In contrast, both Signal and Element provide E2EE as a default across nearly all communications, including group messaging and calls.
Element compared to MS Teams and Signal
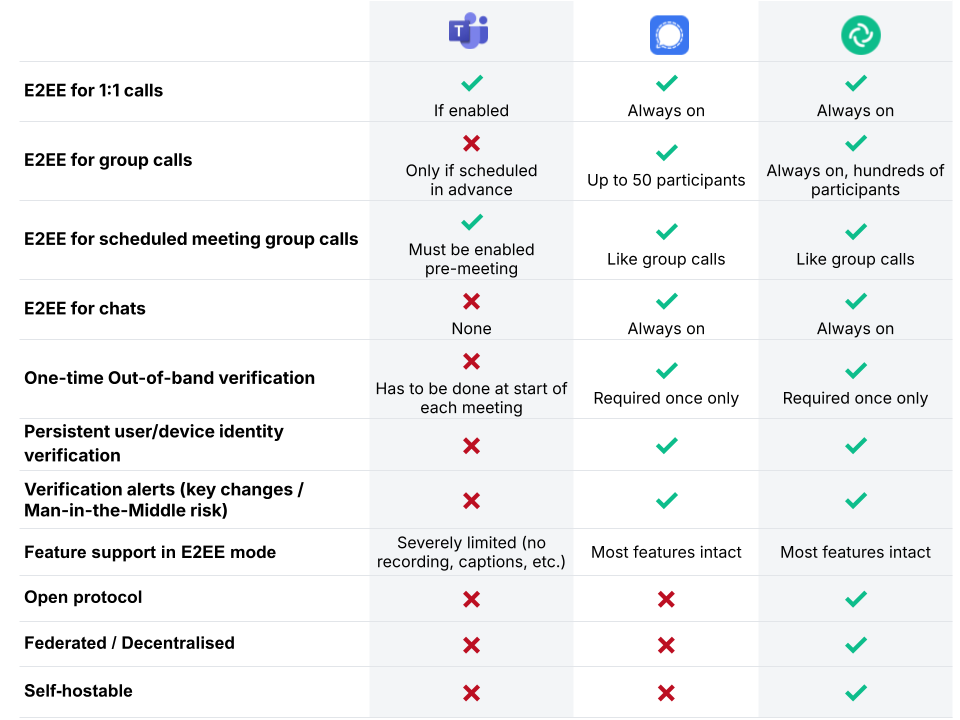
Why it matters
Microsoft Teams’ E2EE is available only in very specific contexts — for instance, 1:1 calls and scheduled calls or video meetings with certain features disabled. Group calls, channel discussions, and most collaborative workflows rely on server-side processing and are not end-to-end encrypted. This is a significant departure from the zero trust model of Element and Signal, where encryption is the default, not the exception.
More critically, Microsoft Teams does not provide persistent identity verification. There’s no long-term storage of verified contacts or devices. This means every time you start an encrypted call or video meeting, you must manually verify a numeric code with the other participant to confirm the connection is secure. Without a second communication channel — like a secure messenger or in-person verification — this step is usually skipped. In urgent or spontaneous meetings, it’s often not practical to verify codes via a second channel, which significantly increases the risk of undetected man-in-the-middle attacks.
There are also strict limitations during encrypted meetings. You cannot add new participants once the session begins — doing so disables encryption entirely. And while the meeting may show a lock icon, this only applies to audio and video. All other parts of the conversation — such as the meeting chat or shared files — are not end-to-end encrypted, which can mislead users into thinking all content is equally protected.
With Element, organisations can even go a step further by self-hosting their own servers. This means they retain full control over the infrastructure, making it physically and legally impossible for any third party — including Element — to compromise or disable the system. It’s a level of assurance that simply isn’t possible with centrally hosted platforms like Microsoft Teams or Signal.
To illustrate: imagine a team discussing a sensitive situation in a Teams Premium encrypted meeting. They see a lock icon and assume everything is secure. But if someone pastes confidential information into the meeting chat or uploads a shared file, that information is not protected by end-to-end encryption — despite the appearance of security. This partial protection model is risky, especially when decisions rely on confidentiality and there is no way to self-host the data. In extreme cases like national security or NGO communication where lives might depend on confidentiality, the reliance on Teams is outright reckless.
Conclusion
If you’re selecting a communications platform with E2EE as a core requirement — for compliance, confidentiality, national security or peace of mind — it’s essential to understand what you're really getting. While Microsoft Teams offers encryption for data in transit and at rest, its E2EE implementation is limited and doesn’t provide the persistent, end-to-end secure experience that tools like Element and Signal do by design.
At Element, we believe end-to-end encryption should be transparent, verifiable, and built into every layer of communication. If you'd like to see what that looks like in practice, we're happy to show you.





